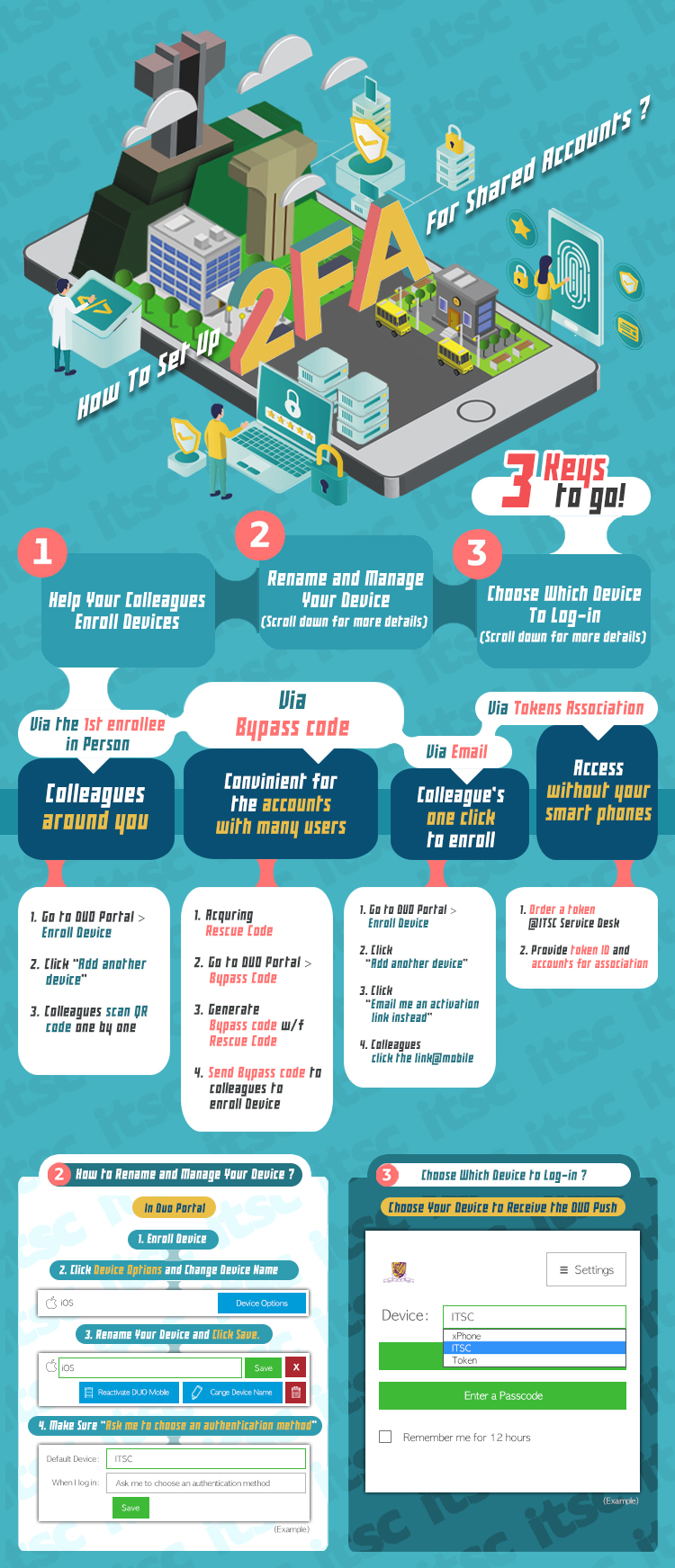
DUO Two Factor Authentication (2FA) | Information Technology Services Centre, The Chinese University of Hong Kong

B digitalization anteckningar - L5, LEGAL ASPECTS FOR DIGITAL TRADE – PART 2, DATA PROTECTION DATA - StuDocu
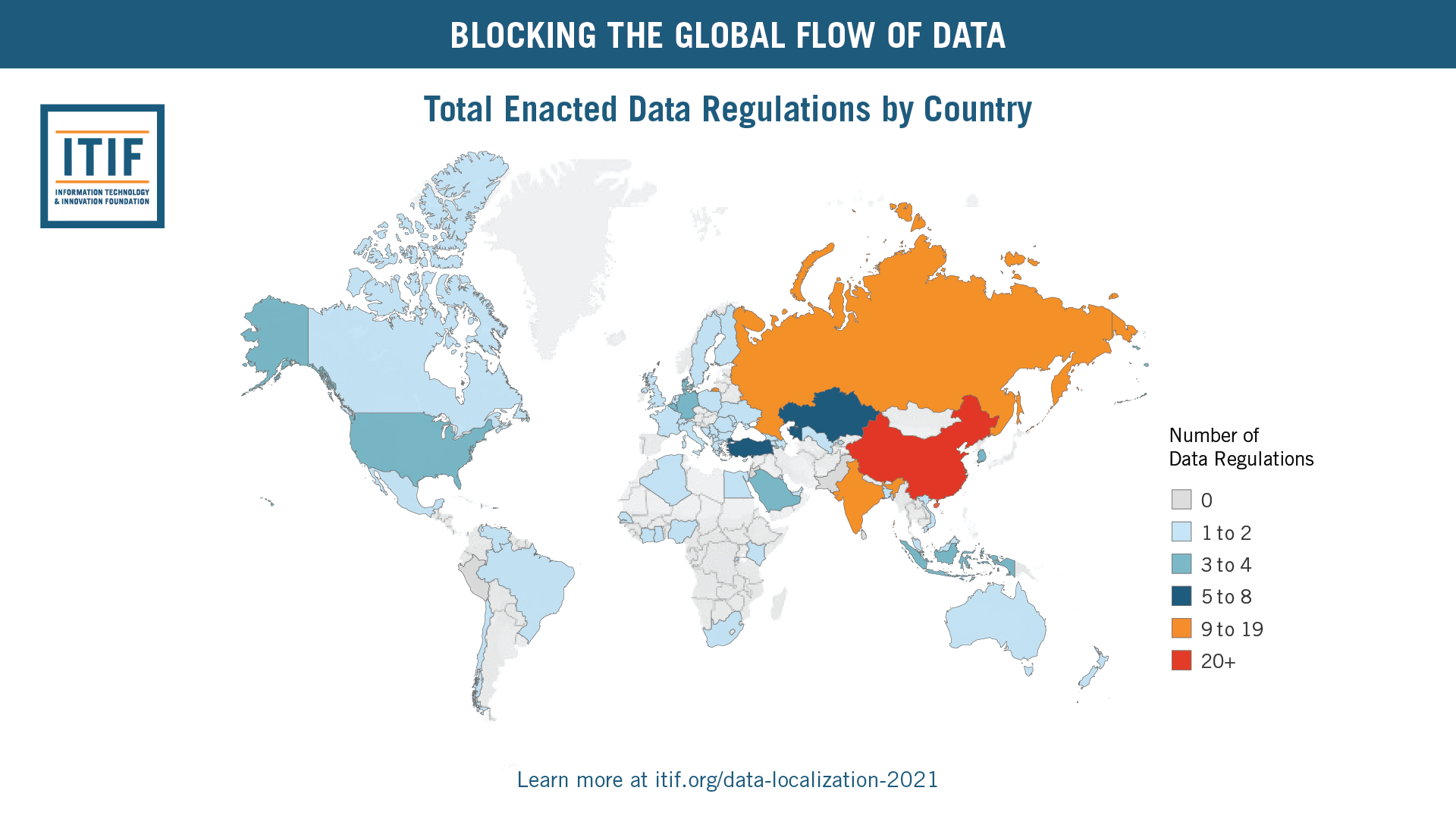
How Barriers to Cross-Border Data Flows Are Spreading Globally, What They Cost, and How to Address Them | ITIF

Data Protector 6.20 Interactive Copy session failed - Data Protector User Discussions - Data Protector
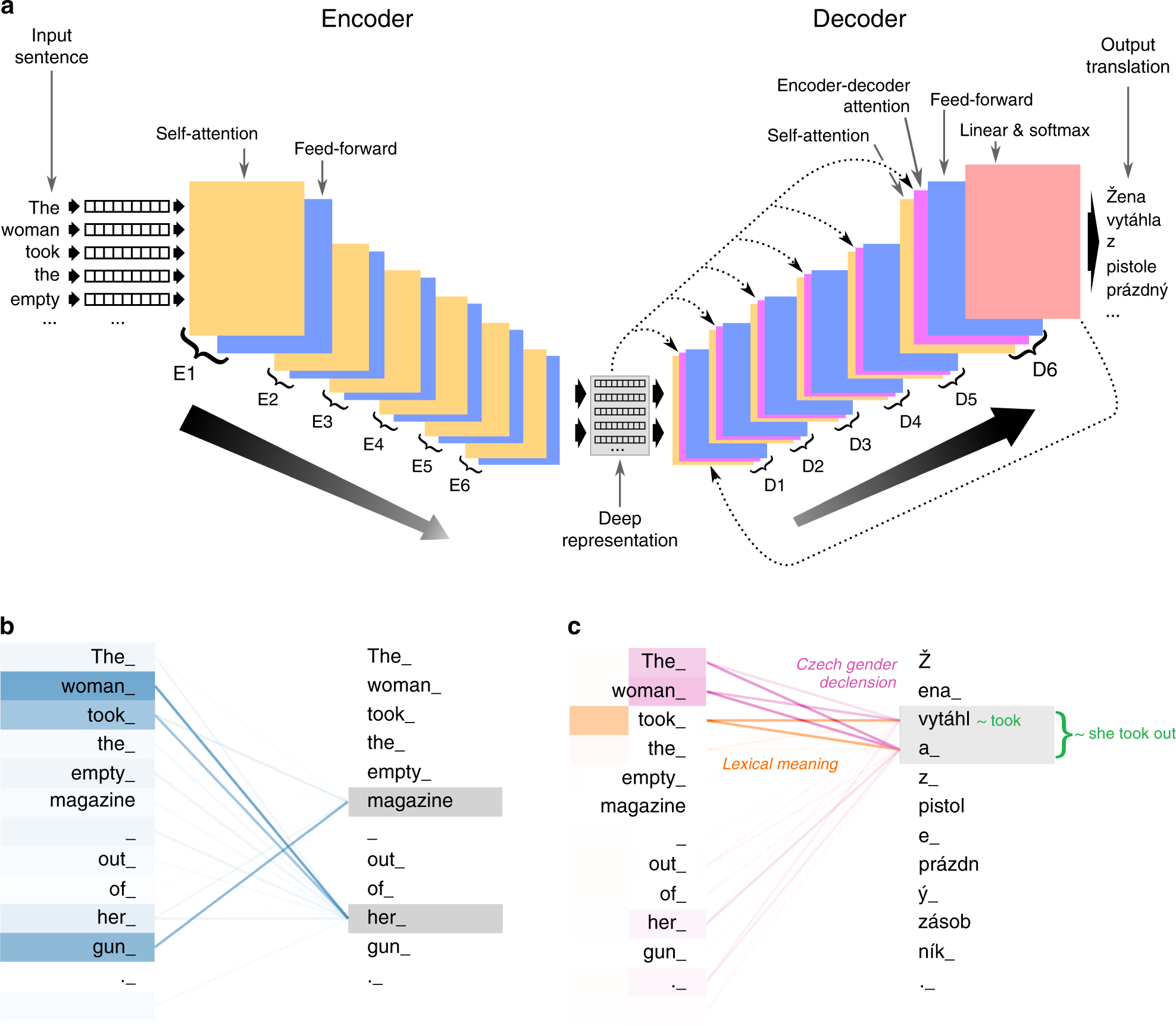
Transforming machine translation: a deep learning system reaches news translation quality comparable to human professionals | Nature Communications